 You
can put anything you like in the “From” header. This is
how a virus might appear to be sending email as you.
You
can put anything you like in the “From” header. This is
how a virus might appear to be sending email as you.The explanations given below will refer to an example email. The email is available here as colourised html and here as raw text. It is a good idea to open one of those in a new tab, window or screen so that you can flip between the example and the explanation.
Viruses are only a serious problem for Microsoft Windows users. Unfortunately, there are a lot of those still around. Eventually they will have switched to something more dependable, but until then we must learn to live with their machines polluting the Internet with viruses.
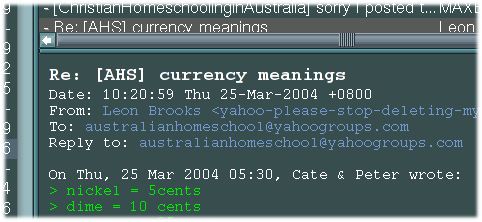
Email has two basic parts, headers and body, separated by a blank line. Emails are made entirely of text, so if an attachment such as an image or a spreadsheet is to be sent, it must be cleverly encoded in text. A header is notionally a line whose first word ends with a colon. One of the headers in the example email says:
To: australianhomeschool@yahoogroups.com
This announces the destination to each program that has to deal with the email, helping it to make decisions about where to send it next. An email message can get by with only a “To” header, but many email servers would look askance at it and perhaps add a “From” header, perhaps trash it.
The “From” header tells the email systems where to send the funereal notice if the email is not able to be delivered. It also tells the recipient who sent the message, and where to send any replies. The email address in the “To” header is “bare”, that is, it has no descriptive name associated with it. There are two ways of making the address more descriptive, and this can be useful if more than one person has to share a mailbox. The “From” header in the example says:
From: Leon Brooks <yahoo-please-stop-deleting-my-subs@leon.brooks.fdns.net>
The “real” email address is embedded in <brokets> (“less-than” and “greater-than” signs). Exactly the same effect could have been achieved by writing it like this:
From: (Leon Brooks) yahoo-please-stop-deleting-my-subs@leon.brooks.fdns.net
If there are any characters other than alphanumerics, spaces or hyphens (“minus signs”) in the description, it’s a good idea to put it in quotes:
From: “Joey ‘Wodger’ Thompson” <wodger@bigpong.com>
Quotes can be included by “escaping” them with a blackslash, like this: “Joey \“Wodger\” Thompson”.
 You
can put anything you like in the “From” header. This is
how a virus might appear to be sending email as you.
You
can put anything you like in the “From” header. This is
how a virus might appear to be sending email as you.
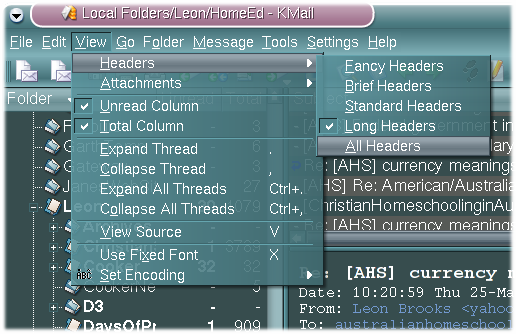
An email program, typically even one used by computer geeks, will normally only display a select few of these headers. KMail, for example, only displays four or five by default.
So how do you tell whether a sending address has been forged? It’s not astronomically difficult, thanks to most email servers adding “Received” headers as the message passes through their metaphorical hands.
The typical life cycle of an email is:
it is created by a Mail User Agent (“mail client”) like KMail, Thunderbird, Outlook, pine or Eudora;
it is handed off to a Mail Transfer Agent (“mail server”) like PostFix, MS Exchange, SendMail, Exim or QMail;
the MTA finds another MTA which admits to wanting mail for that domain and passes it across;
the second MTA finds a mailbox to park it in;
it is fetched and displayed by another MUA.
 Referring
back to the example email, we can see an audit trail of “Received”
headers, last header first, as the message wends its way from me to
Yahoo’s mailing list servers and back again.
Referring
back to the example email, we can see an audit trail of “Received”
headers, last header first, as the message wends its way from me to
Yahoo’s mailing list servers and back again.
Your email client might have a “view all headers” mode which will display all of a message’s headers for your perusal. If not, look for a “View Source” facility, which shows you the entire message in the raw.
The first (bottom) header proclaims mail from “localhost”. Localhost is “this machine”, wherever this machine happens to be, and this says that I run a mail server on my laptop (true), and in fact it even claims to be PostFix (true, but this too could be forged).
The next receipt says “from unknown (HELO lappie.cyberknights.com.au) (203.22.197.45)” but this is partly Yahoo being lazy. The host “lappie.cyberknights.com.au” is what my laptop’s mail server thinks of itself as; the “203.22.197.45” is the IP address of my ADSL router through which the mail passed “without touching” on its way to Yahoo; the “unknown” is Yahoo’s server not bothering to look up that number to learn that my ISP has named it “brooks.arach.net.au”.
The machine noting this claims to be “mta5.grp.scd.yahoo.com” and if you look that up it resolves to 66.218.66.166, an address within a range owned by Yahoo. You can find that out for sure by using “whois 66.218.66.166” on a Unix command line, or finding a WhoIs web form and pasting the number into it.
The next “hop” is to another Yahoo machine called “m6.grp.scd.yahoo.com” and there are hints in this header that the mailer in question is QMail. I’m just guessing, but this is an educated guess, that the first machine was a “bastion” – that is, it fends off Internet attacks and does a first pass at checking that the inbound (to Yahoo) email is sane and presnetable – and the second one does the actual mailing list processing. The next “hop” is an internal one, QMail’s network interface on m6 handing the message off to QMail’s internal message queue manager.
At this point in the record, it is safe to assume that the message is being chewed on by Yahoo’s mailing list manager, probably “n26.grp.scd.yahoo.com”. Now we see “Received” headers for the outbound journey back to me. The first one is “mail.old-firestation.net” – my email server – noting an arrival from n26.
Next we get another “internal” hop noted as “from userid 637”. After my PostFix server decides that a message is for cyberknights.com.au (or whichever of the domains it’s responsible for), it gets handed to a program called AMaViS which supervises a thorough wash and rinse cycle through the Clam anti-virus scanner (ClamAV tosses away up to 300 viruses a day which would otherwise clutter my inboxes) and the SpamAssassin junk-mail filter (SA bins another 600-1000 offers of drugs, enlargements, mortgages and sure-fire stock picks a day). This header is PostFix accepting the shinier, sweeter-smelling messages back to find a box for them.
Then we see “Delivered-To: leonb-fdns@old-firestation.net”, which announces the final resting place of the message, at least until my KMail comes to fetch it.
If you saw a message tracing this kind of path but purporting to come from Sonia, whom we all know lives in clammier climes these days, we could be fairly sure that it was a fake.
This explanation will probably get expanded upon from time to time.